Introduction:
In the dynamic world of software engineering, where data and workloads are constantly growing, efficient data management has become a crucial concern. As developers, we often face challenges in distributing and managing large-scale systems, such as load balancing, failover, and caching. One powerful technique that addresses these challenges is consistent hashing, a revolutionary algorithm that has transformed the way we approach distributed systems.
Consistent hashing is a fundamental concept in computer science that has gained significant attention in recent years. It provides a reliable and scalable solution for distributing data across multiple servers or nodes, ensuring that the impact of changes in the system is minimized. Whether you’re building a content delivery network (CDN), a distributed cache, or a sharded database, understanding and implementing consistent hashing can greatly improve the performance and reliability of your applications.
In this comprehensive guide, we’ll delve into the world of consistent hashing, exploring its principles, use cases, and practical implementation. By the end of this article, you’ll have a solid understanding of this powerful technique and be equipped to apply it in your own projects.
Understanding Consistent Hashing
At its core, consistent hashing is a strategy for distributing data across a network of servers or nodes. The primary goal of consistent hashing is to ensure that when the number of servers or nodes in the system changes, the impact on the data distribution is minimized. This is particularly important in scenarios where the system needs to scale up or down, or when individual servers or nodes are added, removed, or fail.
Traditionally, when using a simple hash function to map data to servers, any changes in the number of servers would result in a significant redistribution of data, leading to high overhead and potential performance issues. Consistent hashing solves this problem by introducing a more sophisticated hashing mechanism that ensures a more even distribution of data across the servers, even when the system topology changes.
let’s visualize the consistent hashing mechanism with a graphical representation.
Here’s a step-by-step flow diagram that illustrates the consistent hashing algorithm:
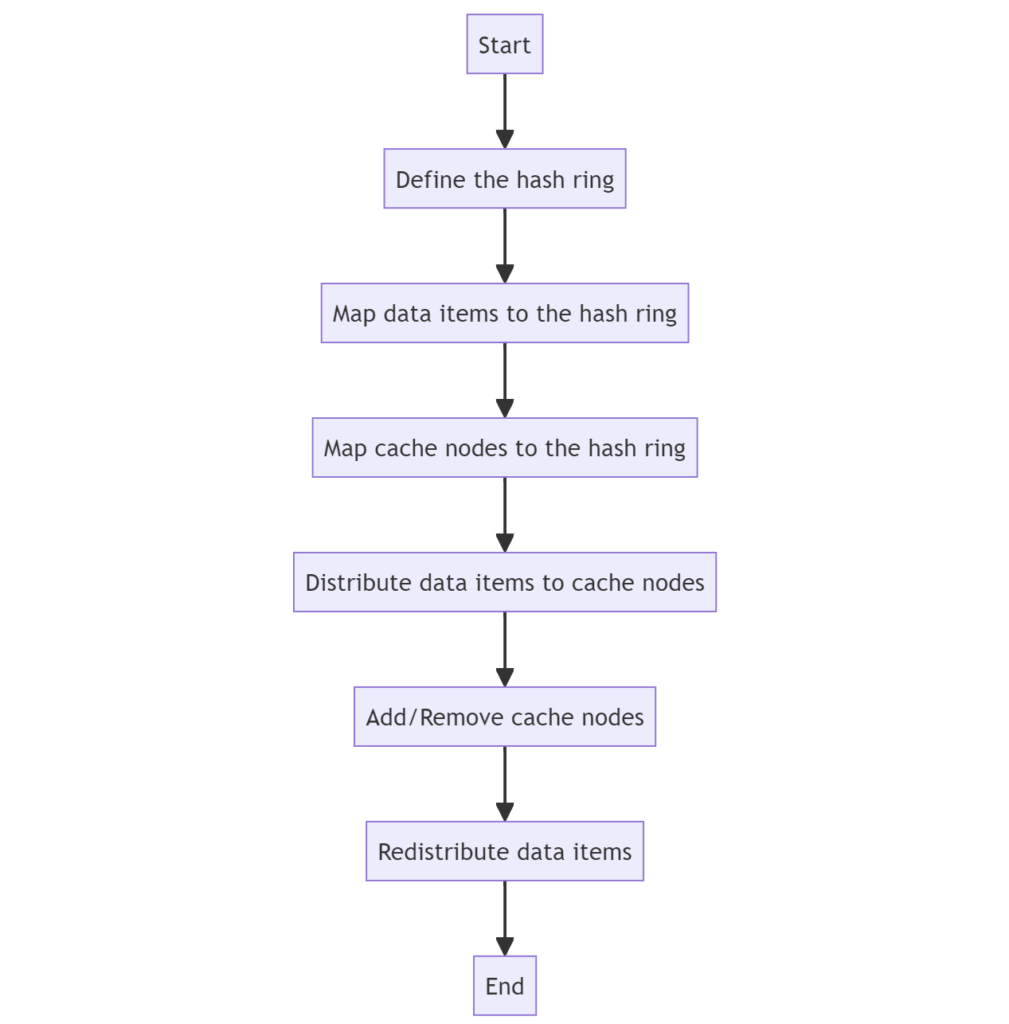
Let’s break down the diagram:
- Define the hash ring: The consistent hashing algorithm starts by defining a circular hash ring that represents the hash space.
- Map data items to the hash ring: Each data item is hashed using a consistent hash function (e.g., SHA-1, MD5) and mapped to a position on the hash ring.
- Map cache nodes to the hash ring: Similarly, each cache node is hashed and mapped to multiple positions on the hash ring, known as “virtual nodes.” This helps to distribute the load more evenly across the cache nodes.
- Distribute data items to cache nodes: The data items are then stored on the first cache node encountered when traversing the hash ring clockwise from the data item’s hash position.
- Add/Remove cache nodes: When a new cache node is added or an existing one is removed, the system needs to handle the changes in the hash ring.
- Redistribute data items: Upon adding or removing a cache node, only the data items that were previously stored on the affected nodes need to be redistributed to the new arrangement of cache nodes on the hash ring.
This graphical representation helps to visualize the key steps involved in the consistent hashing algorithm and how it maintains the distribution of data items across cache nodes, even when the system topology changes.
The use of a circular hash ring and the concept of virtual nodes are the core principles that enable consistent hashing to achieve its goals of scalability, load balancing, and fault tolerance in distributed systems.
The Consistent Hashing Algorithm
The consistent hashing algorithm works by mapping both the data items and the servers (or nodes) onto a common circular hash space, often referred to as a “hash ring.” The mapping of data items and servers is done using a hash function, such as SHA-1 or MD5, which produces a fixed-length output (typically a 160-bit or 128-bit value) that can be used to represent the position of the data items and servers on the hash ring.
The key idea behind consistent hashing is that when a server is added or removed from the system, only a small portion of the data needs to be redistributed. This is achieved by assigning multiple “virtual nodes” to each physical server, which helps to distribute the load more evenly across the hash ring.
Here’s a step-by-step explanation of the consistent hashing algorithm:
- Hash Ring Creation: The hash ring is a circular data structure that represents the hash space. Each data item and server are mapped to a position on this ring using a hash function.
- Data Mapping: When a data item needs to be stored, it is hashed using the same hash function used to map the servers. The data item is then stored on the first server encountered when traversing the hash ring clockwise from the data item’s hash position.
- Server Mapping: Each server is also hashed and mapped to multiple positions on the hash ring, known as “virtual nodes.” This helps to distribute the load more evenly across the servers.
- Load Balancing: When a new server is added to the system, it is hashed and mapped to the hash ring. The data items that were previously assigned to the neighboring servers are then redistributed to the new server, ensuring a more balanced load distribution.
- Failover and Resiliency: If a server fails or is removed from the system, the data items that were previously stored on that server are automatically reassigned to the next available server on the hash ring, ensuring minimal disruption to the overall system.
The key advantage of consistent hashing is that it minimizes the impact of changes in the system topology, such as adding or removing servers. Instead of having to redistribute all the data items, consistent hashing ensures that only a small portion of the data needs to be moved, improving the scalability and reliability of the system.
Use Cases for Consistent Hashing
Consistent hashing has a wide range of applications in the field of distributed systems. Here are some of the most common use cases:
- Content Delivery Networks (CDNs): Consistent hashing is extensively used in CDNs, where it helps to distribute the content (e.g., images, videos, static files) across a network of geographically distributed servers. When a new server is added or removed, the impact on the content distribution is minimized, ensuring a more seamless user experience.
- Distributed Caching: Consistent hashing is a popular choice for implementing distributed caching systems, such as Redis, Memcached, or Elasticsearch. By using consistent hashing to map data items and cache nodes, the cache can be easily scaled up or down without significant data redistribution.
- Sharded Databases: Consistent hashing is often used in sharded database architectures, where the data is partitioned across multiple servers or nodes. This helps to ensure that when the number of servers changes, the impact on the data distribution is minimized, improving the scalability and performance of the database system.
- Distributed File Systems: Consistent hashing is employed in distributed file systems, such as Hadoop’s HDFS or Amazon S3, to manage the placement and replication of files across multiple storage nodes. This helps to maintain data availability and reliability even when the underlying infrastructure changes.
- Load Balancing: Consistent hashing can be used as a load-balancing mechanism, where incoming requests are distributed across a cluster of servers based on the hash of the request data (e.g., the user’s IP address or the URL). This ensures that the load is evenly distributed, even as the number of servers changes.
- Peer-to-Peer (P2P) Networks: Consistent hashing is a fundamental component of many P2P network architectures, such as Chord and Kademlia. It helps to efficiently locate and retrieve data items in a decentralized, self-organizing network.
These are just a few examples of the many use cases for consistent hashing. As distributed systems continue to grow in complexity and scale, the importance of consistent hashing in maintaining the stability and performance of these systems will only continue to increase.
Implementing Consistent Hashing
Now that we have a solid understanding of the principles and use cases of consistent hashing, let’s dive into the practical implementation. In this section, we’ll explore a simple example of how to implement consistent hashing in a distributed cache system using Python.
The code below demonstrates a basic implementation of a consistent hashing-based cache system. We’ll create a ConsistentHashingCache class that manages the mapping of data items to cache nodes and handles the addition or removal of cache nodes.
import hashlib
class ConsistentHashingCache:
def __init__(self, num_replicas=3):
self.num_replicas = num_replicas
self.ring = {}
self.cache_nodes = []
def add_cache_node(self, node):
for i in range(self.num_replicas):
virtual_node = f"{node}:{i}"
node_hash = self.hash(virtual_node)
self.ring[node_hash] = node
self.cache_nodes.append(node)
def remove_cache_node(self, node):
for i in range(self.num_replicas):
virtual_node = f"{node}:{i}"
node_hash = self.hash(virtual_node)
del self.ring[node_hash]
self.cache_nodes.remove(node)
def get_cache_node(self, key):
key_hash = self.hash(key)
sorted_ring = sorted(self.ring.keys())
for node_hash in sorted_ring:
if key_hash <= node_hash:
return self.ring[node_hash]
return self.ring[sorted_ring[0]]
def hash(self, value):
return int(hashlib.sha1(value.encode()).hexdigest(), 16)Let’s break down the implementation:
- The
ConsistentHashingCacheclass has an__init__method that takes the number of replicas (virtual nodes) per cache node as a parameter. - The
add_cache_nodemethod adds a new cache node to the system. It createsnum_replicasvirtual nodes for the given node and maps them to the hash ring. - The
remove_cache_nodemethod removes a cache node from the system. It deletes the virtual nodes associated with the given node from the hash ring. - The
get_cache_nodemethod takes a key as input and returns the cache node responsible for storing that key. It hashes the key and then finds the first node encountered when traversing the hash ring clockwise from the key’s hash position. - The
hashmethod is a simple helper function that uses the SHA-1 hash algorithm to map a value to a 160-bit integer.
Now, let’s see how this implementation might be used in a practical scenario:
# Create a consistent hashing cache
cache = ConsistentHashingCache(num_replicas=3)
# Add cache nodes
cache.add_cache_node("node1")
cache.add_cache_node("node2")
cache.add_cache_node("node3")
# Store and retrieve data
cache.get_cache_node("key1") # Returns "node1"
cache.get_cache_node("key2") # Returns "node2"
cache.get_cache_node("key3") # Returns "node3"
# Add a new cache node
cache.add_cache_node("node4")
# Retrieve data again
cache.get_cache_node("key1") # May return "node1" or "node4"
cache.get_cache_node("key2") # May return "node2" or "node4"
cache.get_cache_node("key3") # May return "node3" or "node4"In this example, we create a ConsistentHashingCache instance with 3 replicas per cache node. We then add three cache nodes to the system and store some data items. When we add a new cache node, the data items are automatically redistributed across the nodes, ensuring a more balanced load distribution.
The key thing to note here is that when a new node is added, only a small portion of the data needs to be moved, rather than having to redistribute all the data items. This is the fundamental advantage of consistent hashing, which helps to maintain the performance and scalability of the cache system as it grows.
Advanced Techniques and Considerations
While the implementation we’ve discussed so far provides a solid foundation for understanding consistent hashing, there are several advanced techniques and considerations that you may want to explore:
- Weighted Hashing: In some cases, the cache nodes may have different storage capacities or processing capabilities. Weighted hashing can be used to assign more virtual nodes to the more powerful cache nodes, ensuring a more balanced distribution of data and load across the system.
- Replica Placement Strategies: The way virtual nodes are placed on the hash ring can impact the overall performance and resilience of the system. More advanced placement strategies, such as power-of-two choices or rendezvous hashing, can be used to further optimize the distribution of data and load.
- Consistency Models: Depending on the use case, different consistency models (e.g., eventual consistency, strong consistency) may be required. Consistent hashing can be combined with other techniques, such as quorum-based replication, to achieve the desired level of consistency.
- Fault Tolerance and Failover: In a distributed system, node failures are inevitable. Consistent hashing can be combined with replication and failover mechanisms to ensure data availability and high reliability, even in the face of node failures.
- Caching Strategies: Consistent hashing can be used in conjunction with various caching strategies, such as Least Recently Used (LRU) or Least Frequently Used (LFU), to optimize the performance and eviction policies of the cache system.
- Hybrid Approaches: Consistent hashing can be integrated with other distributed systems concepts, such as partitioning, sharding, and load balancing, to create more complex and robust architectures.
- Theoretical Considerations: From a theoretical perspective, there are various properties of consistent hashing, such as load balancing, data locality, and convergence, that can be analyzed and optimized to improve the overall system performance.
As you continue to work with consistent hashing, exploring these advanced techniques and considerations will help you build more scalable, reliable, and efficient distributed systems.
Conclusion
In this comprehensive guide, we’ve explored the fundamental concepts of consistent hashing and its practical applications in distributed systems. We’ve covered the underlying algorithm, its key advantages, and common use cases, and we’ve walked through a simple implementation in Python.
Consistent hashing is a powerful tool that can help you tackle the challenges of building and scaling distributed systems, from content delivery networks and distributed caching to sharded databases and peer-to-peer networks. By understanding and mastering this technique, you’ll be equipped to design and implement highly scalable, resilient, and efficient distributed systems that can adapt to the changing demands of the modern digital landscape.
As you continue your journey in software engineering, I encourage you to explore the advanced topics and considerations mentioned in this article, and to experiment with consistent hashing in your own projects. The more you understand and apply this powerful technique, the better equipped you’ll be to tackle the complex challenges of distributed systems.


